This article explains how to configure pinniped supervisor with Keycloak on Tanzu Kubernetes Grid.
Prerequisites
Software versions
- vSphere 7.0.3
- Tanzu kubernetes Grid 1.6.1
- Avi 21.1.4 2p3
- Keycloak: 21.0.0
Environment
- bootstrap machine hostname: tkg161(bootstrap machine is used to run management cluster)
- domain name: hidekazun.jp
Run Keycloak docker image on bootstrap machine
Keycloak must be running with TLS which is required at least for TKG.
Run docker if not running. Create work directory and move to it.
mkdir keycloak
cd keycloak
create self-signed certificate.
echo "subjectAltName = DNS:tkg161.hidekazun.jp" > san.txt
# create key
openssl genrsa 2048 > server.key
# create csr
openssl req -new -key server.key > server.csr
# self sign
cat server.csr | openssl x509 -req -signkey server.key -extfile san.txt > server.crt
create Dockerfile
FROM quay.io/keycloak/keycloak:21.0 as builder
# Enable health and metrics support
ENV KC_HEALTH_ENABLED=false
ENV KC_METRICS_ENABLED=false
# Configure a database vendor
# ENV KC_DB=postgres
WORKDIR /opt/keycloak
RUN /opt/keycloak/bin/kc.sh build
FROM quay.io/keycloak/keycloak:latest
COPY --from=builder /opt/keycloak/ /opt/keycloak/
ENV KC_HOSTNAME=tkg161.hidekazun.jp
COPY server.key /opt/keycloak/server.key
COPY server.crt /opt/keycloak/server.crt
ENV KC_HTTPS_CERTIFICATE_FILE=/opt/keycloak/server.crt
ENV KC_HTTPS_CERTIFICATE_KEY_FILE=/opt/keycloak/server.key
ENTRYPOINT ["/opt/keycloak/bin/kc.sh"]
Let’s build.
docker build . -t mykeycloak:21.0
Run docker image
docker run --name mykeycloak -p 8443:8443 -e KEYCLOAK_ADMIN=admin -e KEYCLOAK_ADMIN_PASSWORD=admin mykeycloak:21.0 start --optimized
Open the URL https://tkg161.hidekazun.jp:8443/ , click Administrator console and login admin/admin.
Configure Keycloak
Create myrealm realm, and myclient client, hidekazun user for authentication. At this time, Root URL, Home URL, Valid redirect URLs, Web origins of myclient client are all blank.
Create management cluster
Update Cluster configuration file as the following and create management cluster as usual by tanzu mc create. preferred_username is the claim in the ID token correspond to the client name.
IDENTITY_MANAGEMENT_TYPE: oidc
...
OIDC_IDENTITY_PROVIDER_CLIENT_ID: "myclient"
OIDC_IDENTITY_PROVIDER_CLIENT_SECRET: "SIQxCyNlFlk02Smgkmit7ZugC6Lqxm92"
OIDC_IDENTITY_PROVIDER_ISSUER_URL: "https://tkg161.hidekazun.jp:8443/realms/myrealm"
OIDC_IDENTITY_PROVIDER_NAME: "keycloak"
OIDC_IDENTITY_PROVIDER_SCOPES: "openid"
OIDC_IDENTITY_PROVIDER_USERNAME_CLAIM: "preferred_username"
After management cluster is created, pinniped-post-deploy-job is completed.
hidekazun@tkg161:~/keycloak$ k get job pinniped-post-deploy-job -n pinniped-supervisor
NAME COMPLETIONS DURATION AGE
pinniped-post-deploy-job 1/1 7s 2d7h
hidekazun@tkg161:~/keycloak$
Update Keycloak setting
Confirm EXTERNAL_IP of pinniped-supervisor service
hidekazun@tkg161:~/keycloak$ k get svc -n pinniped-supervisor
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
pinniped-supervisor LoadBalancer 100.65.87.238 192.168.103.100 443:31639/TCP 3d2h
hidekazun@tkg161:~/keycloak$
Update Root URL, Home URL, Valid redirect URLs, Web origins of myclient client to https://192.168.103.100/callback. This ip address is vary by the environment.
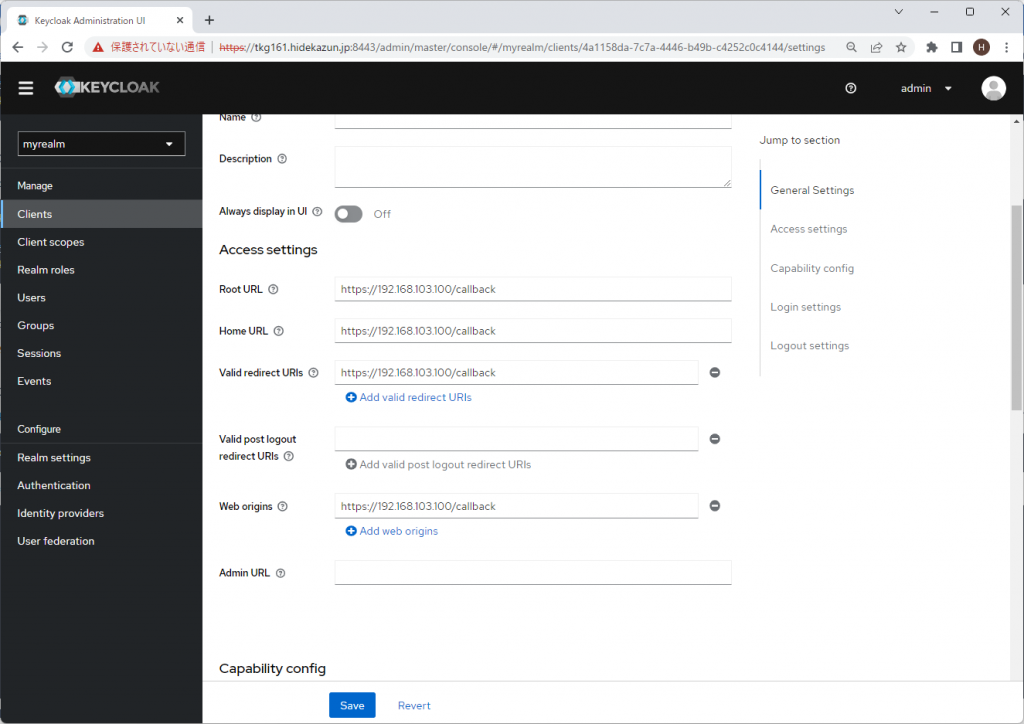
Update pinniped package configuration
As of now keycloak is running by self-signed certificate so that oidcidentityprovider resource ends with error. Pinniped package configuration must be updated to add self-signed certificate.
Get base64 encoded certificate.
hidekazun@tkg161:~/keycloak$ cat server.crt | base64 -w 0
Get values.yaml of pinniped-addon. mgmt1 is managment cluster’s name.
kubectl get secret mgmt1-pinniped-addon -n tkg-system -o jsonpath="{.data.values\.yaml}" | base64 -d > values.yaml
Update values .yaml to add upstream_oidc_tls_ca_data value.
pinniped:
cert_duration: 2160h
cert_renew_before: 360h
supervisor_svc_endpoint: https://0.0.0.0:31234
supervisor_ca_bundle_data: ca_bundle_data_of_supervisor_svc
supervisor_svc_external_ip: 0.0.0.0
supervisor_svc_external_dns: null
upstream_oidc_client_id: myclient
upstream_oidc_client_secret: SIQxCyNlFlk02Smgkmit7ZugC6Lqxm92
upstream_oidc_issuer_url: https://tkg161.hidekazun.jp:8443/realms/myrealm
upstream_oidc_tls_ca_data: LS0tLS......
Let’s apply.
kubectl patch secret/mgmt1-pinniped-addon -n tkg-system -p "{\"data\":{\"values.yaml\":\"$(base64 -w 0 < values.yaml)\"}}" --type=merge
After a while Pinniped package is reconciled and oidcidentityprovider becomes Ready status.
hidekazun@tkg161:~/keycloak$ kubectl get oidcidentityprovider -n pinniped-supervisor
NAME ISSUER STATUS AGE
upstream-oidc-identity-provider https://tkg161.hidekazun.jp:8443/realms/myrealm Ready 70s
hidekazun@tkg161:~/keycloak$
Confirm authentication is running
Execute the following due to running the command on the bootstrap machine.
export TANZU_CLI_PINNIPED_AUTH_LOGIN_SKIP_BROWSER=true
Get kubeconfig file. The point is that –admin option is not added.
tanzu mc kubeconfig get --export-file /tmp/mgmt1-kubeconfig
Let’s execute kubectl.
kubectl get pods -A --kubeconfig /tmp/mgmt1-kubeconfig
URL is shown like the following.
hidekazun@tkg161:~/keycloak$ kubectl get pods -A --kubeconfig /tmp/mgmt1-kubeconfig
Log in by visiting this link:
https://192.168.103.100/oauth2/authorize?access_type=offline&client_id=pinniped-cli&code_challenge=LB5HqUDWH4Kuv58F3FLDcep8h827PVFJbjSmlOmrp6M&code_challenge_method=S256&nonce=385e448cc0071a83475620c4d0d20efa&redirect_uri=http%3A%2F%2F127.0.0.1%3A36991%2Fcallback&response_mode=form_post&response_type=code&scope=offline_access+openid+pinniped%3Arequest-audience&state=3b8edd9d472ef250da6a674e2d3a6a0b
Optionally, paste your authorization code:
Open the URL. Additional operations would be needed due to self-signed authenticate.
Login by hidekazun user created on Keycloak.
Code is shown.
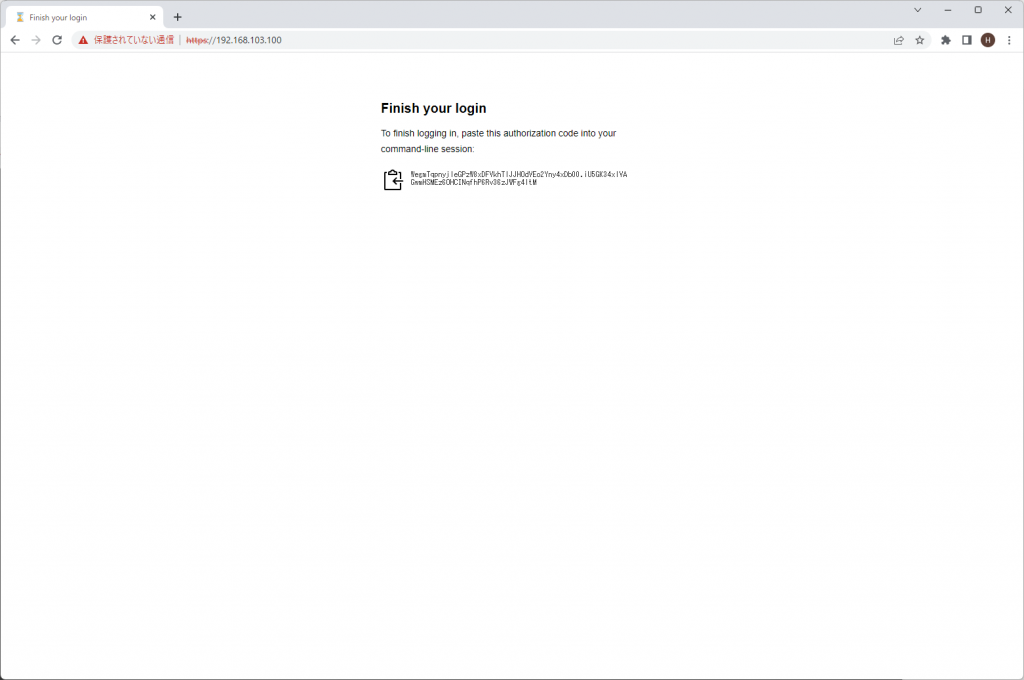
Copy the code and paste after Optionally, paste your authorization code:
hidekazun@tkg161:~/keycloak$ kubectl get pods -A --kubeconfig /tmp/mgmt1-kubeconfig
Log in by visiting this link:
https://192.168.103.100/oauth2/authorize?access_type=offline&client_id=pinniped-cli&code_challenge=LB5HqUDWH4Kuv58F3FLDcep8h827PVFJbjSmlOmrp6M&code_challenge_method=S256&nonce=385e448cc0071a83475620c4d0d20efa&redirect_uri=http%3A%2F%2F127.0.0.1%3A36991%2Fcallback&response_mode=form_post&response_type=code&scope=offline_access+openid+pinniped%3Arequest-audience&state=3b8edd9d472ef250da6a674e2d3a6a0b
Optionally, paste your authorization code: WegmTqpnyjleGPzW8xDFVkhTlJJHOdVEo2Yny4xDb00.iU5GK34xlVAGwmHSMEz6OHCINqfhP6Rv36zJWFg4ltM
Error from server (Forbidden): pods is forbidden: User "hidekazun" cannot list resource "pods" in API group "" at the cluster scope
hidekazun@tkg161:~/keycloak$
hidekazun user does not have any privileges so that the error is shown. If appropriate privilages are added, pods would be shown.